1. Problem
You want to understand the
process for creating business rule policies. These policies are core
components to all business rule development.
2. Solution
The business rules framework consists of policies, rules, vocabularies, and facts. A business policy
is the container in which business rules are defined, versioned,
tested, deployed, and executed. From within the business policy editing
window, the first step before creating rules is to create a policy. The
policy then may contain one or more rules for deployment. To create a
policy, take the following steps:
Open the Business Rule Composer by selecting Start => Programs => Microsoft BizTalk Server 2010 => Business Rule Composer.
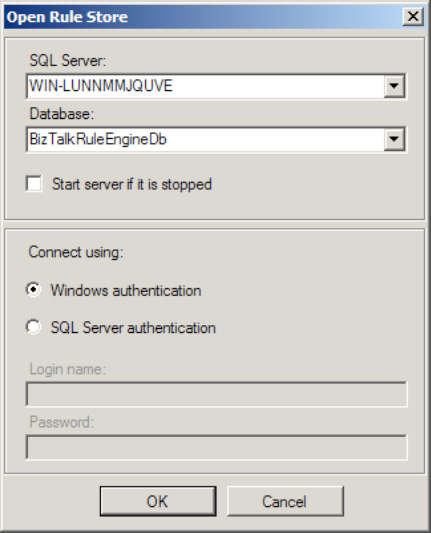
If the Open Rule Store dialogue box opens, enter the correct connection information (see Figure 1).
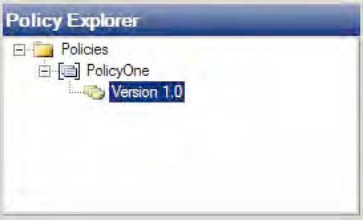
Within the Policy Explorer, right-click the Policies node, and click Add New Policy and give the policy a name.
By
default, version 1.0 of the policy is created. You may change the
version number if you want by selecting the version, navigating to the
Properties window, and setting the Version property.
Right-click the version, and choose Save. See Figure 2.
3. How It Works
Creating a business rules
policy is a relatively simplistic exercise but is the foundation to the
business rules framework. Once you have created the policy, you can add
rules and facts to the policy for testing and deployment. When calling
the policy from BizTalk, the latest version will be selected for
execution, unless you specify a specific version. The rules engine
detects and deploys new versions of a policy, allowing changes to be
made to the business policy in a live, deployed process. This creates a
powerful environment to apply a dynamic business policy to deployed
solutions with minimal work.